Spanning all sectors of security
Due to our unique combination of hands-on experience, years of education and seamless communication, our team can provide every type of security, individually tailored to your unique requirements.
Open Source Intelligence
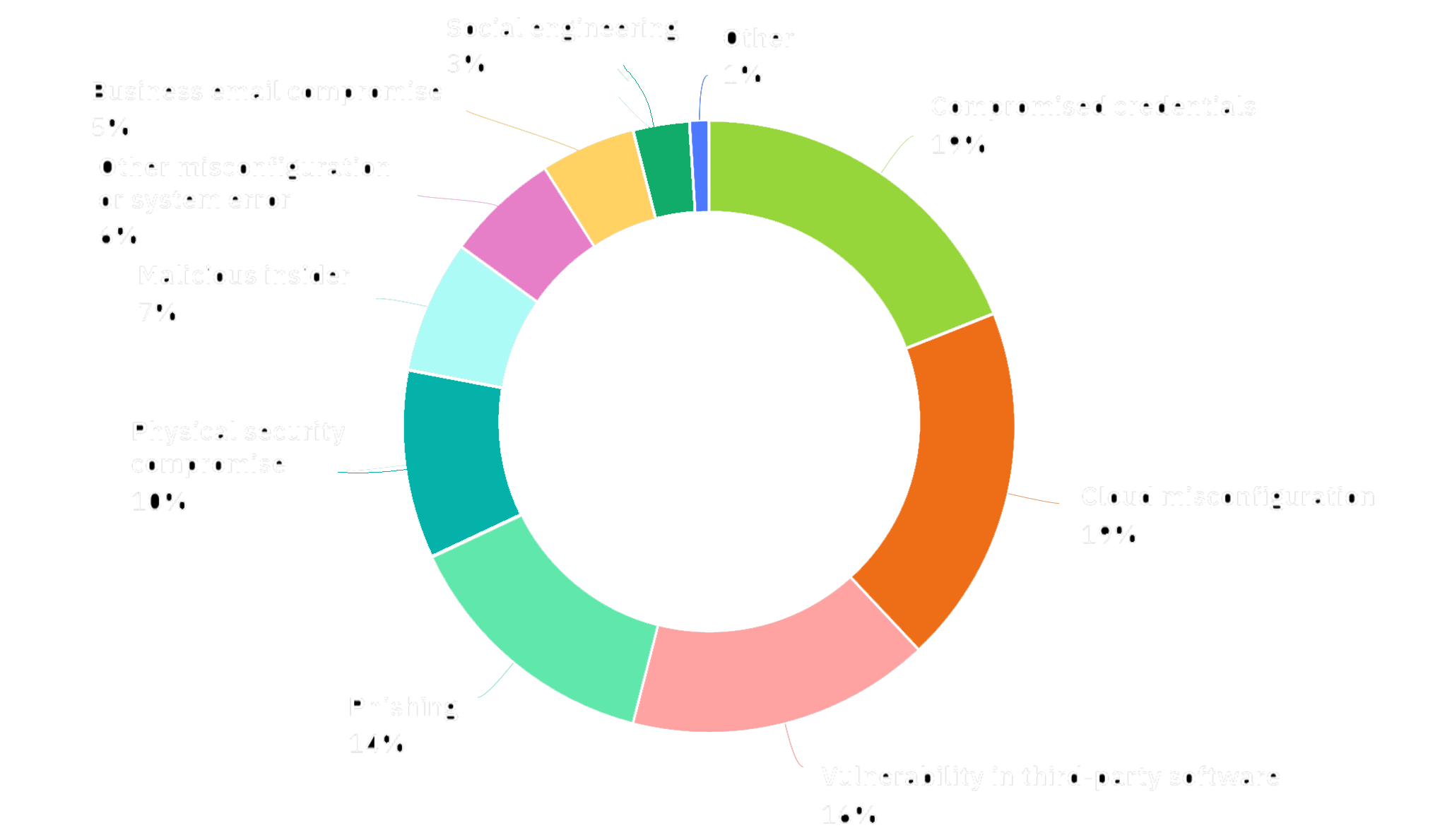
The ability to find and compile any and all information pertaining to you, or your business that's currently available online. We will scour both the surface and dark web tirelessly, to ensure our OSINT audits cover everything, including things you didn't even know where online yet or information intentionally hidden.

Network Auditing
Our team will audit your businesses network in an attempt to find vulnerabilities, and how to mitigate them, as well as scan the network for any malware that may already exist.

Operational Security
To provide the best auditing possible for your business, our team will enact risk assessment by posing as threat actors, finding vulnerabilities in your access controls and pre-existing security measures, and help you mitigate them every step of the process.